BITCOIN PRICE 2140
For the First Time in The Security World, We provide compliance services remotely and budget friendly for startups.
View More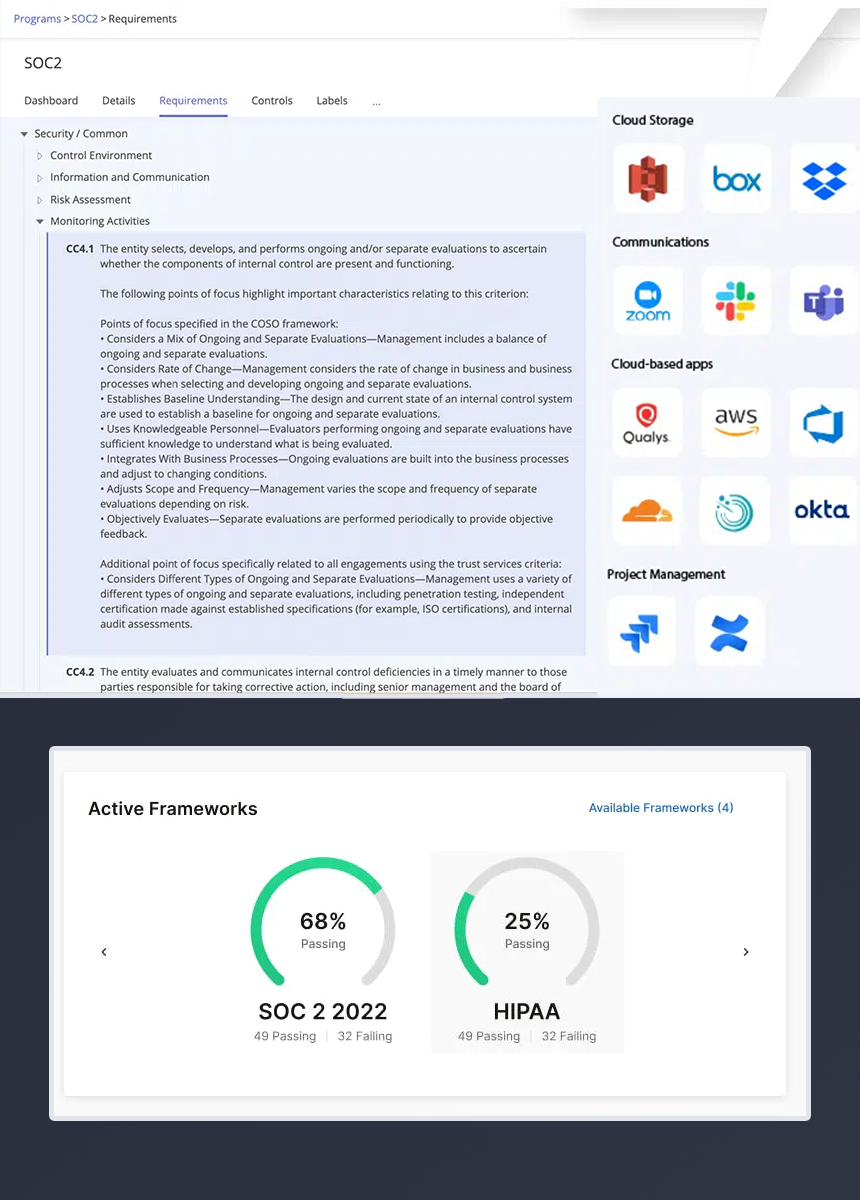
A new brand powered by famous service providers in the market
During the Corona epidemic, obtaining compliance faced a serious problem, of course, startups had to spend a lot of money to get this certificate and the complexity of this process was very high. Now, with the help of an experienced team and a strong network and support, we were able to provide a system to reduce costs and complications. And we are ready to provide our services to startups across the world.
Fastest Path to Become Compliant

CIS compliant organizations will have an established baseline for protecting their systems and data from cyberattacks.
Read More
or ISMS is a collection of standards designed to provide guidance to organizations looking to implement strong cybersecurity.
Read More
give consumers the right to ask companies for information held about them. Within a month's time, companies must be able to fulfill the request.
Read More
is a standard developed by AICPA, based on: security, availability, processing integrity, confidentiality, privacy, and how to manage customer data.
Read More
is a set of security standards designed to ensure that ALL companies that accept, process, store or transmit credit card information maintain a secure environment.
Read More
a federal law that required the creation of national standards to protect sensitive patient health information from being disclosed without the patient's consent or knowledge.
Read More
gives consumers more control over the personal information that businesses collect about them and the CCPA regulations provide guidance on how to implement the law.
Read More
NIST Cybersecurity Framework (CSF), provides private sector organizations with a structure for assessing and improving their ability to prevent, detect and respond to cyber incidents.
Read More
development of secure and resilient federal information systems. These controls are the operational, technical, and management standards and guidelines information systems use to maintain confidentiality, integrity, and availability.
Read More
a contractual obligation for contractors handling CUI on their networks and these organizations are expected to conduct self-assessments to determine and maintain compliance.
Read More
adhering to the rules and standards set out by the Federal Financial Institution Examining Council. Failure to comply with these standards can result in fines and penalties for a financial institution.
Read More
is a program is aligned to DoD's information security requirements for DIB partners. It is designed to enforce protection of sensitive unclassified information that is shared by the Department with its contractors and subcontractors.
Read More
is a compliance initiative to regulate how the data of a Microsoft employee, customer or vendor is being handled by Microsoft partners and vendors.
Read More
If you need a custom compliance framework that is related to a specific regulatory or government, we will handle it easily.
gateio

Become Compliant Just in Few Weeks
 Budget & Time Friendly for Startups
Budget & Time Friendly for Startups
 No Complexity
No Complexity
 No Hidden Fee
No Hidden Fee
 Fully Free Prepration and Consultant
Fully Free Prepration and Consultant
 Automated Process With Help of AI
Automated Process With Help of AI
 Zero Trust Remote Audit
Zero Trust Remote Audit
 Simple Continious Compliance and Monitoring
Simple Continious Compliance and Monitoring

Obvious Advantages/Disadvantages
All Type of Companies






All Type of Companies









For the First Time in The Security World, We provide compliance services remotely and budget friendly for startups.
View More
With Sectify Mapping Controls System Your Start-Up Can Get Multi-Compliances in Once ...
Read More
Remote Audit, Budget Friendly in Few Weeks Become Compliant with Sectify....
Read More© Sectify 2024 All Rights Reserved